2018 has been an active year for vulnerabilities, malware, and other scams. Yesterday, a new variant Bip Dharma, was discovered by Michael Gillespie, a well known ransomware watchdog. This particular variant appends all encrypted files with a .Bip extension. The malware itself scans for any data files, such as standard Word, Excel, photos, or other files, and encrypts them.
This variant is considered particularly serious because of it’s ability to encrypt shared network drives that are not even mapped to the affected computer. It will also encrypt a virtual machine’s host drives, making it extremely dangerous if a virtual server is infected. This means this ransomware acts similarly to the GrandCrab variant that appeared earlier this year. Even worse, this ransomware will actually delete any volume shadow copies (previous versions of files) on the machine as to prevent any restoring from an earlier local machine backup.
What to Look Out For?
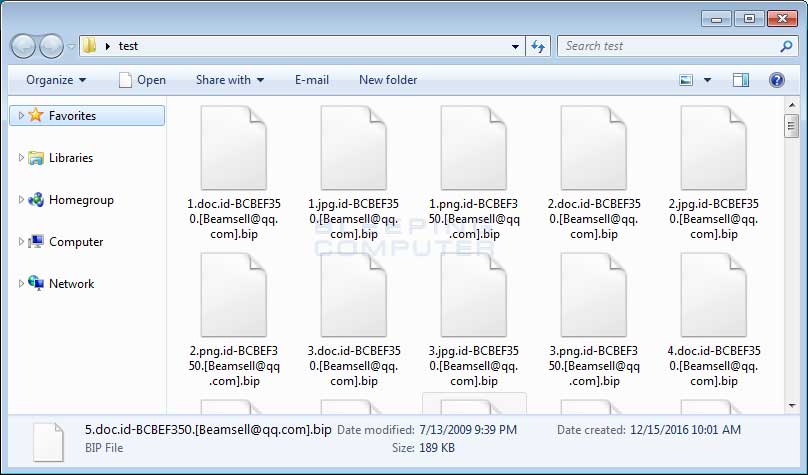
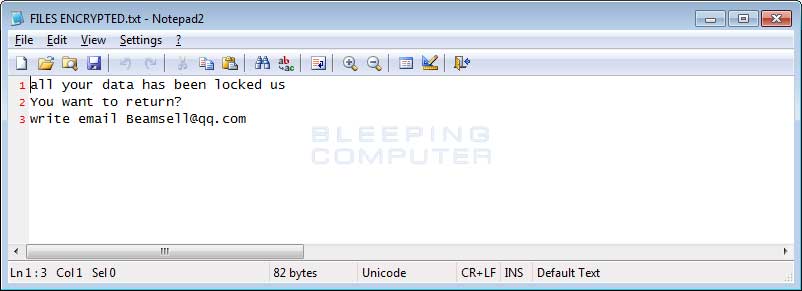
When a machine is infected, you’ll notice the file structure will appear as they do in the image above, with the e-mail address to decrypt the files right in the file name (Beamsell@qq.com), the .Bip extension, and the original file name. There are also two separate ransom notes left on the machine. The first is Info.hta, which launches automatically when any user logs into an affected machine, and the second, a text file named FILES ENCRYPTED.txt. The ransomware will run at every log on, encrypting any new files it has access to over the network or locally on the machine, so it’s imperative that all infected machines be removed from the network immediately!
Decrypting Files
As with most ransomware, there currently exists no way to freely decrypt any of the encrypted files. Currently, you must rely on proper backups. Without a proper backup of files, it is impossible to retrieve without paying the ransom. As this is a new variant, it is currently unknown whether or not a real decryption hash key is provided upon paying the ransom.
Staying Safe from Ransomware
VMX Technologies clients: We have you covered. With functioning, regularly checked backups, endpoint and network security measures in place, and a team of technicians working behind the scenes to ensure Windows Updates are installed and antivirus is running, there is little that can bring you to a halt. However, nobody is exempt from ransomware, and there are still measures you can take to ensure you’re protected.
- Backups are key — backup regularly and often. Make sure you’re saving your files to a backed up location such as a server or cloud storage.
- Check for Windows Updates regularly — These are security updates and are absolutely essential.
- Allow your antivirus to do it’s job– leave it enabled so it scans your downloaded files and documents
- Do not open an attachment from somebody you don’t know. Let someone know if it looks suspicious.
- Don’t re-use passwords. Nobody wants to regularly change their password but a weak password can seriously impact your personal and professional life.
If you have more questions, you are always welcomed and encouraged to reach out to VMX Technologies at 856-719-1955, or by e-mailing support@vmxtechnologies.com. Technicians are always available and standing by to assist you with your issues.

